Wyze camera breach allowed customers to look at other people's camera feeds: What to know
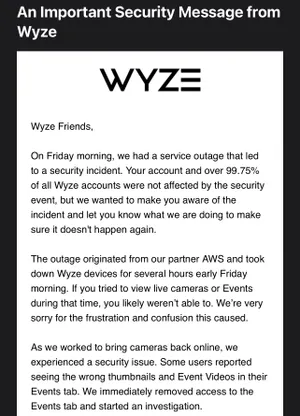
Wyze users were able to see into the homes of others after an outage that overloaded the company's servers and corrupted user's data, according to the company's press release.
The company also says the security breach is much worse than what was first anticipated.
"About 13,000 users received thumbnails from cameras that were not their own," said Dave Crosby, one of the company's cofounders, in a statement.

The company states it sent out several rounds of emails. The order depended on how and if the user was affected.
- The first email went to all users who were not affected by the glitch.
- A second was sent to those whose thumbnails were made available to other users, but those thumbnails were not tapped on.
- Then a third email was sent to users whose event thumbnails were made available to others and were tapped on.
- Finally, a fourth email was sent to users who had thumbnails that weren't their own made available to them.
Who is affected by the Wyze camera breach?
Users who were affected should've received an email, but Wyze's digital community manager said users could see a "slight" delay when receiving their email.
In the email sent out to users, the security company states around 99.75% of its users remained unaffected by the breach.
Originally, the company thought only 14 users could see into other people's homes, but around 13,000 users received thumbnails that weren't theirs. Of those users, 1,504 tapped on it. The company states that most only enlarged to an image, but some were able to see footage from another user's camera.
"We've identified your Wyze as one that was affected," read the email sent to the 1,504 users who had their video viewed. "This means that thumbnails from your events were visible in another Wyze user's account and that a thumbnail was tapped."
The videos that were seen were not live-feeds. They were snippets of events that triggered the camera to start recording.

"To make sure this doesn’t happen again, we have added a new layer of verification before users are connected to Event Video," reads each email that was sent out Wyze users. "We have also modified our system to bypass caching for checks on user-device relationships until we identify new client libraries that are thoroughly stress tested for extreme events like we experienced on Friday."
How did the camera breach happen?
We had a caching issue from a third-party caching client library that was recently integrated into our system," said Crosby in the statement. "It got overloaded after the outage Friday morning and got wires crossed while trying to come back online."
The company blames the outage that occurred on Friday which led to the security breach on its web host provider and partner, AWS.
AMC Networks lawsuit email:Here's what it means to you
Wyze's previous security breaches
This isn't the first time Wyze has faced a security breach.
In 2022, a class-action lawsuit was filed over allegations stating Wyze knowingly concealed a vulnerability that allowed hackers to view images and videos stored in memory cards, reports Bloomberg Law.
According to Spice Works, the company settled the suit in March 2023

Julia is a trending reporter for USA TODAY. She has covered various topics, from local businesses and government in her hometown, Miami, to tech and pop culture. You can follow her on X, formerly known as Twitter, Instagram and TikTok: @juliamariegz.
Disclaimer: The copyright of this article belongs to the original author. Reposting this article is solely for the purpose of information dissemination and does not constitute any investment advice. If there is any infringement, please contact us immediately. We will make corrections or deletions as necessary. Thank you.







